As you probably already know, the best way to shield your machine against malware threats is to protect the TCP layer accesses with a good Firewall and having a great AntiVirus & AntiMalware software installed, such as BitDefender and MalwareBytes (both free for personal use). For further info about how to protect your system against them, I strongly suggest to read this post.
Despite these valid countermeasures, there's still a chance that you can get infected, for example if the malware manages to enter to your system by exploiting one of the various "temporary" folders provided by your OS to install new applications, unzipping compressed archives, store temp data and so on.
Here's a list of the "risky" folders on a typical Windows machine:
- C:\Windows\Temp, which is arguably the most common executable path for viruses & malwares, and all its subfolders.
- %USERPROFILE%\AppData\Local\ and all its subfolders.
- %USERPROFILE%\AppData\Roaming\ and all its subfolders.
Since all these folders are meant for storage and not for executables to run, finding a way to prevent potentially harmful .exe files from running from them would definitely be a good extra layer of defence. Luckily enough, Windows (and Windows Server) allows us to do that using the Software Restriction Policies, a set of rules that can be configured using the Group Policy Editor.
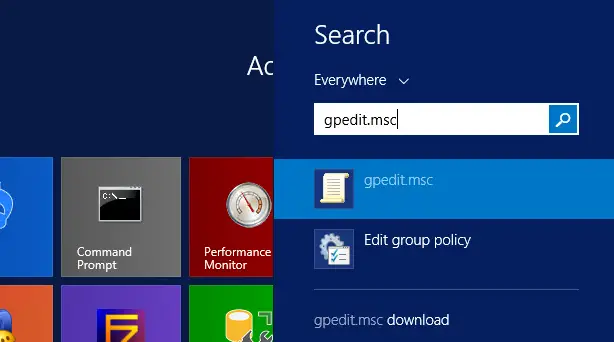
To do that, search for gpedit.msc and execute it:
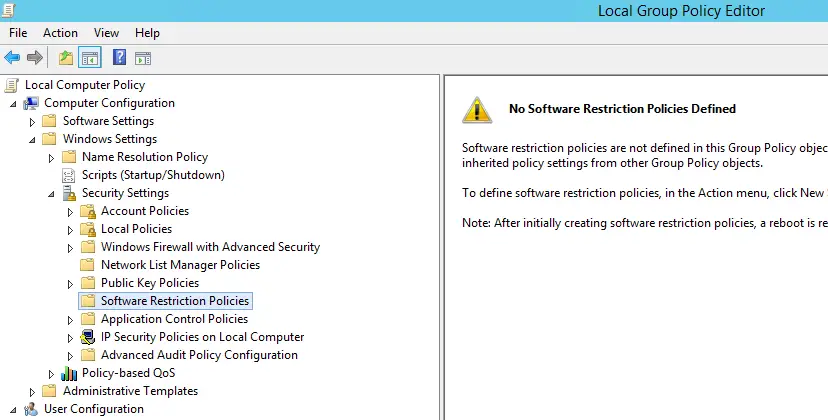
Navigate through Computer Configuration > Windows Settings > Security Settings > Software Restriction Policies:
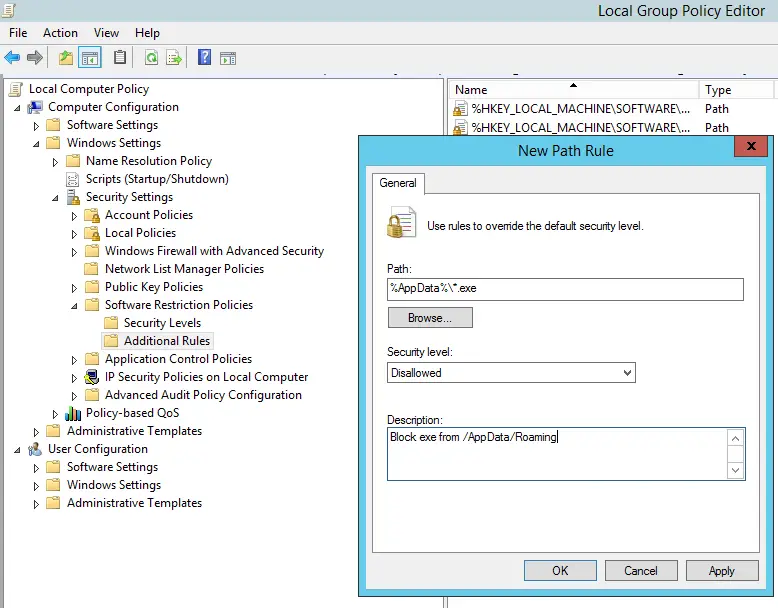
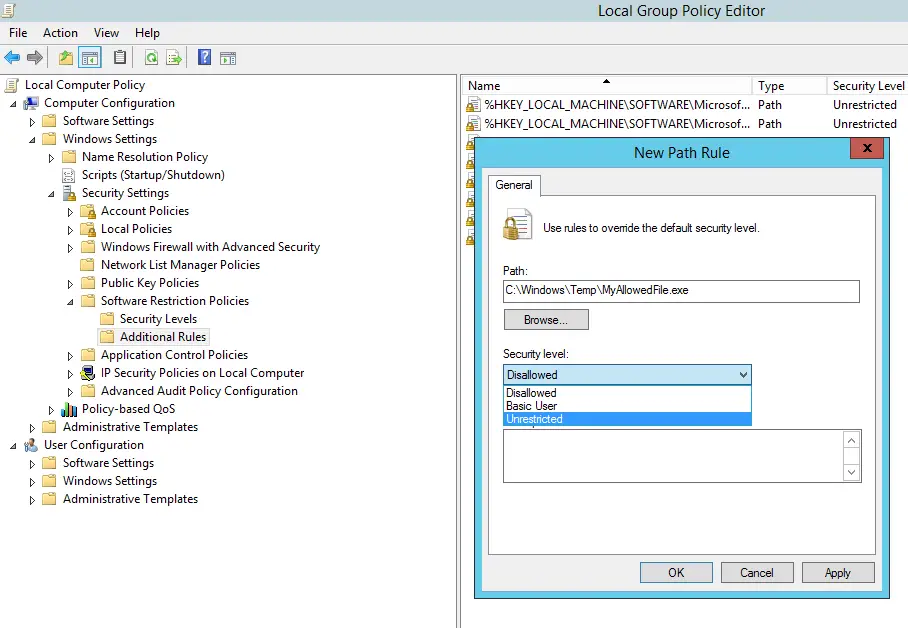
If there are No Software Restriction Policies Defined, as you can see in the above screenshot, right-click to the folder node and select New Software Restriction Policies in the contextual menu. Doing that will create some new subfolders; right-click to the Additional Rules, choose New Path Rule... and enter, one after another, the paths that you want to prevent executable files to run from. Make sure to put the *.exe at the end, so that you will only block executable files.
I strongly suggest to block (at least) the following:
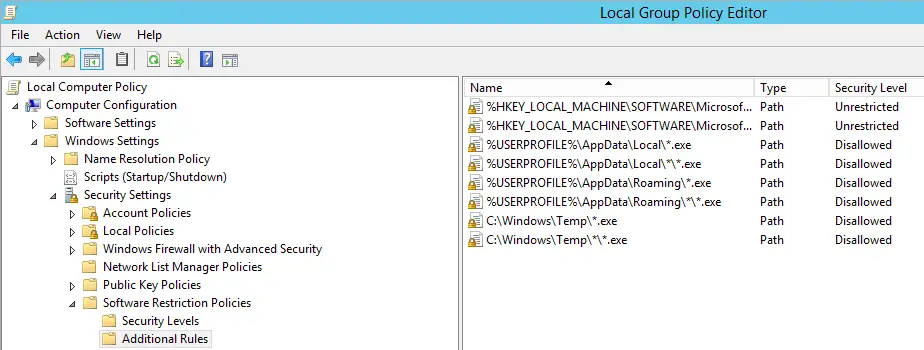
- C:\Windows\Temp\*.exe
- C:\Windows\Temp\*\*.exe
- %USERPROFILE%\AppData\Local\*.exe
- %USERPROFILE%\AppData\Local\*\*.exe
- %USERPROFILE%\AppData\Roaming\*.exe
- %USERPROFILE%\AppData\Roaming\*\*.exe
We can see all these rules in place by looking at the screenshot below:
This will block most potentially unsafe executables from running, including those coming from archive attachments opened using the Windows built-in zip support.
Exceptions & exclusions
What if we want to allow some specific executable files to run in these folders? The answer is simple: just create an exception by adding an unrestricted entry, such as in the following screenshot:
That's about it: I sincerely hope that this post will help users, enthusiasts and administrators in making their machines more secure against the most common virus, malware and ransomware threats!



Thank You so much! Your article helped solved a problem that I have been fighting with for weeks.
-Lok