Now that we use the web for (almost) everything, using secure and strong credentials has become an absolute must. Typically, when we adopt this fundamental cybersecurity best practice, we always think about strong and non-guessable passwords - since this is what we consider the most important thing to protect against the most known threats (guessing attempts, brute-force techniques, rainbow tables, and the likes). This is the common approach among all kinds of users, including software developers, and it's definitely a good practice: that's also the reason that drove us to create our very own C# Random Password Generator library for ASP.NET Core & ASP.NET MVC.
However, what about usernames? Contrary to popular belief, using a secure, hard-to-guess username can definitely improve our security posture against most credential breach attempts. That's the reason why the guys behind 1Password - one of the most used SaaS password managers available nowadays - released a neat Random Username Generator free online tool. No, we're not fooling around: such a tool does actually exist, and it's also the topic of this post.
Using the tool
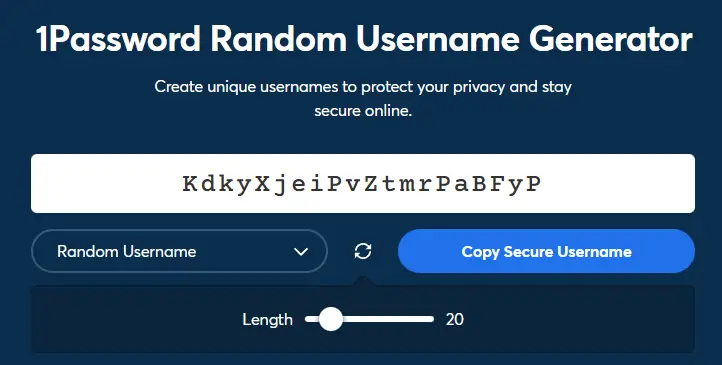
Using the 1Password's Random Username Generator tool is incredibly easy: you just have to visit the tool's official page with your favorite browser and you'll get your randomly-generated username ready to copy and paste wherever you like.
As we can see, we can even configure the length (default is 20 characters) and the type of username we want to generate:
- Random Username (the default choice)
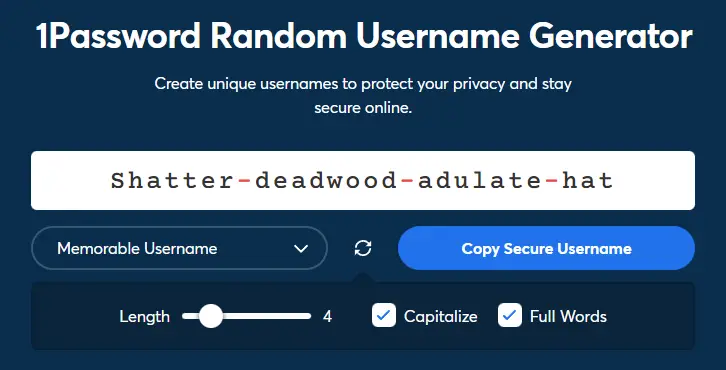
- Memorable Username (some random easy words separated by a dash)
The Random Username type is more secure, it will be protected against dictionary-based brute-force attacks; however, the Memorable alternative is definitely easier to remember (and say to others).
It's worth noting that, should you choose the Memorable route, you'll be able to access additional settings - such as choosing the number of words used, capitalizing them or not, as well as using full words or readable chunks (for increased protection against the brute-force attacks we've mentioned a short while ago).
Now that we know how the tool actually works, it's time to answer some fundamental questions: do we really need to use it? And why?
Why should I use this tool?
As a matter of fact, the short answer is: YES, you should seriously consider using it - at least for the websites (or services) storing some sensitive or important data.
If you think about that for a second, you'll easily understand why: as long as your username is public (and it often is), any attacker will be able to easily fetch it; even if it's not public one some services, it might be public in other services where you have used the same username (just like the well-known password bad practice, remember?), thus making the attacker able to retrieve it with some basic research. For that very reason, using a securely generated username together with a strong, unique password for every account will definitely increase your security posture against most online threats, including - yet not limited to - brute-force attempts.
Needless to say, using unique usernames and passwords for every account might be difficult: however, as long as you are using a password manager (such as 1Password) to keep track of passwords, you are already set - you'll just have to keep track of usernames as well!
Conclusion
Using a unique (and complex) username together with a unique (and complex) password will definitely increase your protection against online threats, such as brute-force attempts and credential stealing attempts - thus reducing the risk of data breaches. It's important to understand that such good practice applies to all kinds of users - web surfers, software developers, system administrators, as well as anyone who wants to increase its security posture against hacking attempts and online threats.