The recent Windows 10 updates released in May 2018 have introduced some improvements to the security of some protocols, eliminating problems related to known vulnerabilities. Among these, new security rules have been introduced on some CredSSP protocol vulnerabilities in the RDP authentication phase, better known as Terminal Desktop or Remote Desktop.
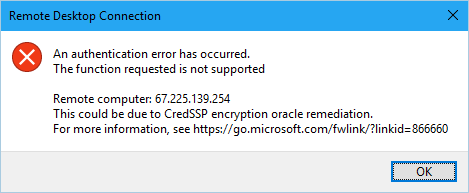
Unfortunately this has caused for a large number of users the appearance of the following error when making a remote connection via RDP:
An authentication error has occurred. The function requested is not supported
Remote computer: <computer name>
This could be due to CredSSP encryption oracle remediation.
For more information, see https://go.microsoft.com/fwlink/?linkid=866660
This post is dedicated to understanding the causes of this error and the various possibilities of solution.
Understanding CredSSP
CredSSP stands for Credential Security Support Provider protocol and is an authentication provider that processes authentication requests for other applications. In vulnerable versions of CredSSP there is a problem, identified recently, that allows remote code execution: an attacker who exploits this vulnerability can forward user credentials to execute code on the target system. Any application that depends on CredSSP for authentication may be vulnerable to this type of attack.
To fix the issue the following updates have been recently released by Microsoft:
- B4103721 for Build 1803
- KB4103727 for Build 1709
- KB4103731 for Build 1703
- KB4103723 for Build 1609 and Windows Server 2016
Additional info on the vulnerability are available at this link: 2018-CVE-0886.
The Solution
The most streamlined and secure way to get rid of the error and to be able to connect via RDP is to ensure that both the client and the server have installed the update: this is by far the safest solution, as it solves the problem while keeping all the security protocols enabled.
In the event that it is not possible to intervene on the server, it is possible to resolve in another way, by deactivating the protected CredSSP mode on the client and thus forcing the authentication in unsafe (vulnerable) mode. Needless to say, this is a workaround that should be used only temporarily, for example to restore the connection needed to install the new patch on the server.
To force the non-secure mode of CredSSP authentication, follow this procedure:
- Click on Start, then Run (oppure tasto Windows + R) and type gpedit.msc
- In the mask that will appear, select COMPUTER CONFIGURATION –> ADMINISTRATIVE SETTINGS –> SYSTEM –> CREDENTIALS DELEGATION; once there, select CredSSP encryption oracle remediation in the rightmost section of the window.
- In the modal window that will appear, select ENABLED and then, in the dropdownlist below, select VULNERABLE, just like in the screenshot below:
In case gpedit is not available - for example, if we're using Windows 10 Home Edition - we must manually create (or modify) the AllowEncryptionOracle registry key in the Windows Registry. To do this, follow the instructions below:
- Click on Start, then Run (oppure tasto Windows + R) and type regedit
- Navigate through HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\CredSSP\Parameters\
- Create the AllowEncryptionOracle key (or change it, if already present) by setting its value to DWORD 2 (the default value should be 1).
Alternatively, we can download and execute this .reg script which does the exact same thing. Remember, however, that this is only a temporary workaround, which we should promptly uninstall - by removing the AllowEncryptionOracle key to DWORD 1 - as soon as we've correctly patched the connecting server.
That's it for now: happy connection!