Table of Contents
We couldn't complete our VPN review & test-drive series without talking about NordVPN, one of the most renowned VPN services in 2019: from PCMag to TechRadar, from VPNMentor to CompariTech, everyone seems to love NordVPN speed, performance and reliability. Are the rumors really true? We tried our best to find it out within this review and test-drive.
In the unlikely case you don't know what a VPN as-a-service actually is we strongly suggest to check out this post before going further: once done, come back here to read the review to its full extent.
Internet without borders
Advanced security, Internet freedom, Complete privacy: this is the payoff of the NordVPN website, and it fits well with the company spirit. NordVPN was born in 2012 when four childhood friends came together to build technology that could liberate the internet. Spending a lot of time in different parts of the world they saw internet censorship, content control and intrusive government surveillance growing faster than ever before. The feeling that the internet was losing its main purpose led to a search of possible solutions on how to overcome all the restrictions.
After setting up the first VPN server and sharing the prototype among their friends, the creators started receiving extremely positive feedback and were encouraged to continue their work. That’s how NordVPN was born, now serving more than 12 million people worldwide.
The NordVPN name was inspired by Nordic ideals of confidence, trust, and innovation: it reflects how we value our customer freedom of choice, how we strive to be innovative with our technology and the way we work. Over the years, NordVPN became a trusted online security solution, used by over 12 million internet users worldwide. Meanwhile, NordVPN became recognized by the most influential tech sites and IT security specialists. It is now one of the most trusted privacy and security service provider in the world, known for the strongly held values and well thought-out features.
Ethical purposes
Before starting with the technicalities, we would like to briefly review the NordVPN manifesto which can be found on their website.
We, at NordVPN, strive to make Tim Berners-Lee’s vision of a truly open internet a reality. Mr. Berners-Lee imagined the internet as a very different place when he implemented the first successful HTML communication in 1989. It was to be a safe space, free from censorship and surveillance. Unfortunately, as headlines around the world demonstrate daily, this is hardly the case these days.
At NordVPN, our team of mathematicians and technologists wake up every morning with one core goal – to keep the internet as free as possible. This is our passion and why we come to work every day. We strive to provide absolutely uncompromised safety and privacy on the Web. We make sure no one sees what you do online because they shouldn’t. Nor should we, for that matter.
For this reason we do not keep logs. If someone asks us about you, we have nothing to share. We are free internet enthusiasts who believe in a common secure future online. We support fighters for human rights, journalists, volunteers in conflict zones, information activists or anyone who believes in the power of the open Web as Mr. Berners-Lee imagined.
In the spirit of transparency, we’ll do everything we can to keep you updated about all aspects of our service, from server status upgrades to occasional glitches. We aim to create a lasting relationship of mutual trust with you, the customers who share our deeply held values.
Additional ethical contents can be found on their social responsibility page, where they talk about freedom of speech, digital education & awareness, social reports, and so on: definitely a commendable display of good efforts... However, it's about time to bring the numbers and the stats in.
Data Security
NordVPN was the first VPN service to describe their data protection features as military-grade encryption... which might sound a bit exxagerated, yet it's not that far from the actual truth. As a matter of fact, NordVPN protects their users data using AES, an encryption standard used and approved worldwide by governments, cybersecurity experts, and cryptography enthusiasts: more specifically, NordVPN makes use of AES with 256-bit keys, which is recommended by the NSA for securing classified information.
The number 256 refers to the key size, so 256-bit has 1.1×1077 possible combinations. While it is true that any key can be broken given enough resources, cracking AES with 256-bit keys is definitely out-of-reach nowadays: to break it, a good hacker would need to use supercomputers that would countinuously work for many (billions of) years.
Two security protocols
Like most VPNs, NordVPN creates a tunnel to transmit your data to VPN servers securely. When this happens, two different security protocols are used to determine how that tunnel is actually formed: IKEv2/IPsec and OpenVPN. More specifically, IKEv2/IPsec has been adopted as a default in NordVPN iOS and macOS apps, while OpenVPN is the default for NordVPN Windows, macOS, and Android apps. Both of these protocols have their pros and cons, but each one of them is dependable and highly recommended by most IT security experts worldwide.
IKEv2/IPsec
IPsec, which stands for Internet Protocol Security, operates with the newest version of the Internet Key Exchange (IKEv2) to enhance security, stability, and speed. IKEv2/IPsec employs powerful cryptographic algorithms and keys, which are almost unbreakable - even by today's supercomputers. With computing power continuously increasing, and cryptography breakthroughs always around the corner, it’s important to stay one step ahead. That’s why NordVPN uses the very adaptable Next Generation Encryption (NGE) with IKEv2/IPsec: this will add an additional layer of security, because the protocol will mantain its resiliency even when the CPU computational capacity will increase over the natural course of time.
OpenVPN
OpenVPN is an extremely versatile security protocol, which you can use both for TCP and UPD ports – for safe browsing, gaming, and live streaming. To guarantee the protection of your sensitive data, NordVPN uses AES-256-GCM encryption algorithm with a 2048-bit DH key. The whole global cybersecurity community has a stake in OpenVPN since it has an open source code, which is freely available for review and modification. With every new bug report, with every new-found vulnerability, with every line of code, this security protocol gets stronger and better. We can definitely say that transparency is the most powerful OpenVPN feature.
Verdict
Although using AES-256 is definitely a good thing, it also became the de-facto standard among the top-tier VPN service providers. The same can be said for IKEv2/IPsec and OpenVPN: both protocols have been adopted by most VPN services as well. Therefore, we can say that NordVPN data-encryption level is great, yet it's pretty much on-par with most of its competitors nowadays.
Features
This is a list of NordVPN's most important features.
DoubleVPN
One of the NordVPN most distinctive features is called DoubleVPN. Typically, when you connect to VPN, your traffic travels through a remote VPN server, which changes your IP address and encrypts all the data that you send or receive over the internet. Due to this setup, no snoopers or cybercriminals can see what you are doing online. With Double VPN, your online activity hides behind two servers instead of one, using a two-layered connection pattern known as VPN server chaining. The working principle is rather simple:
- Your traffic reaches a remote VPN server and leaves it securely encrypted.
- The encrypted traffic then passes through a second VPN server and gets encrypted one more time.
- You reach your internet destination securely and privately.
It goes without saying that such tecnique drastically increases the overall security of the connection, as well as the anonymization standards: however, it also comes with a noticeable performance decrease - which is often well-worth the trade.
These are the most distinctive benefits of the DoubleVPN feature:
- Double encryption: the transmitted data is protected with an extra layer of encryption, thus making it twice as hard for hackers to decipher.
- Enhanced security: the connections are mixed between UDP and TCP protocols, which increases the security level of all the online activity.
- IP masking: As the caller's actual IP address was changed by the first VPN server, the second server doesn’t have any information about it.
- Increased privacy: Nobody, including the caller's ISP can see the final destination of the web requests issued by the caller: they can only know that a VPN service is being used.
Kill Switch
The Kill Switch is a fundamental characteristic of any good level VPN: such function provides the automatic shutdown of one or more applications (or the internet connection, or the entire PC) whenever the VPN connection ends for any reason. It essentially acts as a safety net that will protect the transmitted data against accidental disclosure in case of connection problems.
Strict No-Log policy
Without a VPN, all your online traffic passes through your internet service provider (ISP): they can see everything you do online and track your behavior. Sometimes they even hand your internet access data over to advertisers, government agencies, or other third parties. When you connect to a VPN server, your ISP can no longer see what you do on the internet. However, your VPN provider does have that power. So it’s crucial to know what kind of logs – details about you and your online activity – the provider keeps.
NordVPN operates in Panama, where there are no legal requirements for collecting user data: this basically means that they are free to apply a no-log policy, meaning they won't register their users activities at all. This is a really good thing for users privacy, because no government will be able to force NordVPN to hand over your online activity records.
CyberSec
A recently introduced feature that blocks certain threats (malware or phishing) automatically: it should acts just like an antivirus + a firewall IPS system. Unfortunately, we were unable to properly test it (we'll edit this section if we'll be able to do that in the near future).
Custom DNS
A neat feature allowing the user to add their own custom DNS servers to be used instead of NordVPN's DNS servers.
P2P-Friendly servers
P2P stands for Peer-to-Peer networking. It is one of the fastest and most convenient ways to share files with large groups of people. Normally, each user would download a file from one server or a network of servers. With P2P, each downloader also becomes an uploader, making the process of file sharing much more efficient.
The reputation of P2P sharing is somewhat negative, which is why many internet service providers (ISPs) try to discourage users from it. But file sharing has valid and perfectly legal uses – in fact, the P2P technology is ideal for public distribution of free-access data, sharing large amounts of corporate data internally, and also pushing software updates to massive user bases. That being said, you still need to think about safety measures while sharing or downloading files from a P2P network.
The main issue is that every device uploading or downloading the same file on a P2P network can see each other’s IP address. That’s the very nature of P2P – it wouldn’t work otherwise. So what’s great for efficient information sharing is not that great for your privacy. Besides, your internet service provider can also quickly detect that you’re using P2P. They may deny access to file-sharing websites or set bandwidth limits, which slows down your internet speed.
With these risks in mind, if you use P2P, VPN should be your best friend for (at least) three reasons:
- IP address masking. When you enable a VPN, you connect to a remote VPN server, replacing your real IP address with that of the server. This IP swap hides your location and helps you stay private while sharing files or simply browsing the web.
- Bandwidth throttling protection. When you use a VPN, your ISP can’t detect that you are sharing files and shape your connection accordingly. This way, you can avoid the annoyance of bandwidth throttling and internet roadblocks.
- Online traffic encryption. With a VPN, P2P files and all other data you send and receive travels through a strongly encrypted tunnel. That means no one can get their hands on your private information.
6-Device rule
A single NordVPN account will cover up to six devices at once. Moreover, if you connect NordVPN to your router, it will secure every device on your network, using up only a single space out of the 6 available. Considering how many devices are available within a single family nowadays, this is indeed a good thing, as you can secure the whole home with a single account.
Top-grade Assistance
NordVPN customer service has been given the Best Customer Service 2018 Award by bestVPN.com: their agents are ready to help you 24/7 (all day, every day) using a deedicate line: they also have a pretty good Help Center & Support page which can be useful to quickly find the answers for most frequently asked questions.
VPN Client
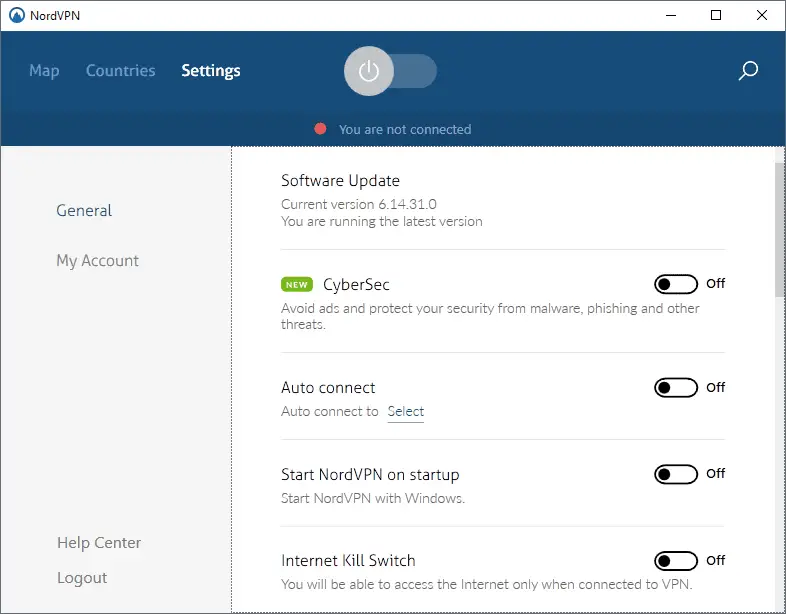
The NordVPN Client is definitely a big deal, expecially if we compare it to the "minimalistic" approach chosen by most VPN service providers - which is not ideal when you have to play with a lot of options. It comes with Server List section with favorites and bookmark support, and a well-presented Settings page which can be used to customize the various connection properties and features.
Here's a list of the most important features you can control from the Settings section:
- CyberSec
- Custom DNS
- Auto connect
- Kill Switch (App and Internet)
- Invisibility on LAN. This useful feature hides the computer on the local area network.
- Obfuscated Servers. It can be used to use NordVPN from restricted locations (we couldn't try that since our country is not restricted).
- Notifications. This option can be activated t o get connect and disconnect notifications in the SysTray.
The Server List section provides a country-specific server lists, dividing them in four different types:
- Dedicated IP address. These servers have a dedicated IP addresses that don't change.
- Double VPN. These servers will chain the VPN connection so that traffic flows through two VPN servers all the time (as previously explained in the Double VPN paragraph).
- Onion over VPN. These server will allow you to use TOR while connected to the VPN.
- P2P. These servers supports P2P traffic (not all do).
Performance Tests
The test-drive which we carried out was mostly performance-oriented: we were interested to measure the ability of the VPN to maintain a decent speed over time with a wide range of different applications: Torrent, Emule/eDonkey, web surfing in HTTP and HTTPS mode , FTP, SFTP, RDP connections, TeamViewer sessions, online gaming (using CounterStrike: Global Offensive, MTG Arena and Hearthstone) and video streaming platforms (Netflix, Amazon Prime Video, CrunchyRoll, Youtube Red).
We have to admit that the results were top-notch - probably the best we ever got from a VPN service as of today. Let alone the online FPS-based gaming, which remains substantially out of the question for all VPN services as the ping rate drops below the acceptable minimum levels (150-300 latency), the speed drop was rather minimal. We got a ~10% speed decrease in WWW browsing and FTP/FTPS download, and ~15% speed decrease with the P2P applications: in some cases (BitTorrent), the ISP throttling bypass allowed us to record even better performances than the non-VPN connection - which was also great.
Conclusions
NordVPN lives well up to its fame: a blazingly-fast, secure and reliable VPN service with no noticeable downsides, thus being well-worth the price. For all these reasons, we highly recommend it to anyone who is looking for a top-tier VPN service!