Table of Contents
The term malware - crasis of malicious software - is used in the IT field to indicate any software created with the express purpose of causing damage or unwanted effects to a computer, to the data it contains or to the operating system used. Over the last few years, the word has gradually replaced the definition of virus, previously used for a long time and substantially improper if used too generally: computer viruses are a particular type of malware, that is, they represent a small part of a very large family which includes a variety of types of software with very different characteristics that share the purpose described above: damage or undesirable effects, which may mean malfunctions, loss of information and / or operation, system block, illicit acquisition of information, violation their privacy or even, more simply, an apparently harmless computer parasitism aimed at abusing the connection or interactions of the unfortunate operator.
This article, far from offering itself as a universal remedy for all the countless infections that run on the net, was created with the aim of providing the reader with some useful advice on the two main aspects of protection from this type of threats: prevention and treatment.
Prevention
Having a good malware protection (and/or antivirus software) is certainly a wise choice, however you shouldn't believe that it would be enough. Conversely, the presence of antivirus software often accustoms the average user to forget the most important aspect of prevention, that is, the responsible and conscious use of their system. Concept that, in practical terms, translates into a series of habits that must necessarily be adopted by every user, operator, family member or friend who will use the PC.
E-Mail attachments
Statistics do not lie: despite the awareness campaigns, the countless articles published every year in specialized magazines and the e-mail checking functions present in all the main antivirus, more than half of the "infections" are still transmitted today using techniques based on sending e-mail messages. They range from the trivial case of attachments conveyed through email spoofing techniques - in which the sender pretends to be our bank, a courier who warns us of a package in stock, a friend of friends and so on and so forth. - to situations much more complex and difficult to identify, such as messages from real people - almost always relatives or friends - who have been previously "infected" and who have our address in their address book. The latter cases are particularly critical: if the experience has led many people to be wary of "famous" and notoriously spoofed senders such as Poste Italiane, Banca Sella or GLS, the same cannot be said when the e-mails come from known senders . There is only one solution to defend against this type of attack: it is necessary to become even more experienced, developing a particular "eye" that allows us to recognize spoof attempts on the fly. Here is a short list of things to check out.
The Sender
Learn to check the sender of every message you receive very well when opening it: many malware recover your address on the network or from your friends' address book, but only a small part of them is able to simulate a truly credible sender. Check the correspondence of the first name and last name (if any), and above all the e-mail address(es) present in the From field, making sure to check the letters carefully: remember that most spoofing is designed to abuse selective reading techniques that each of us more or less consciously puts into practice when he is in front of his computer, especially when reading e-mails and browsing websites: therefore be very careful not to be fooled by the various @micosoft.com, @googIe.com, @yaahoo.com and so on. Don't make the mistake of overestimating your level of attention: be humble and get used to paying attention to what you read.
The Syntax
In most cases, spoofing e-mails are produced - by the thousands - by sites, services or programs based on automatic text generators, moreover almost always not developed in Italy. This means that, nine times out of ten, the message you will receive will contain a large number of spelling and syntax errors: badly declined verbs, masculine instead of feminine and vice versa, wrong conjunctions ... luckily for us, Italian is a very difficult language to "program". Learn to make the most of this territorial advantage by recognizing and discarding all sorts of ungrammatical or syntactically inconsistent emails on the fly. Whenever you read something suspicious in the body of the message, take a look at the sender (see previous point) and ask yourself the question: "would this person / bank / courier really write like this?" Do not make the mistake of justifying it, perhaps thinking that she was on her cell phone and / or on the move: a person who is in a hurry rarely sends attachments from his cell phone. Pay close attention to what you receive, especially if it is not something you have been waiting for (see next point).
The Attachment
Here's another question you need to get used to asking yourself: "How many times do you get an attachment you weren't expecting from that person / bank / courier?" The answer, in most cases, is: very few. Whether it's invoices, courier receipts, or vacation photos, these are all things that under normal circumstances you know you should receive. Don't make the same mistake as those people who can't wait to say: "with all the e-mails I get, I definitely can't waste time with such a trivial issue ...". A phrase that those who work in the field of IT security hears repeated more and more often by their customers, to the point that it is sometimes enunciated as if it were a source of pride, as if those who deal with really important things cannot afford to waste time with them. trifles. There is nothing more wrong and shortsighted than this belief: on the contrary, when a person makes the decision to manage their private life and / or work activity through the IT tool, being able to understand what they receive with due awareness and attention becomes a fundamental element of their professional ability. Anyone who is unable to do so, either due to inexperience or the fault of a quantity of e-mails received far exceeding his or her ability to manage, is a person who lives and works beyond his capacity: anyone who is not in provided that he can determine with a reasonable degree of certainty whether the file he received is an important thing he was waiting for or a fraud attempt is inevitably destined, sooner or later, to feed the burgeoning malware market. It's just a matter of time ... unless he has the humility to remedy the situation, working on his shortcomings and becoming a better operator.
Scamming & Phishing
Getting used to checking these details not only helps to defend against spoofing techniques aimed at distributing malware but also to recognize scamming and phishing attempts, two no less dangerous online scam techniques: in order not to go off topic here we will just summarize the meaning of these two expedients, postponing a more exhaustive treatment to a subsequent article.
- The term Scam refers to those scams based on social and / or behavioral engineering techniques aimed at inducing people to carry out certain actions immediately - usually investments or small donations - on the basis of advantages or prospects of gains in the making. This definition includes all the most common scams, from the economic declinations of the chains of Saint Anthony / Ponzi scheme (and variants), passing through the Nigerian (and derivative) scams up to the scams based on pyramid marketing fraudulent techniques.
- The term Phishing describes those scams that try to convince victims to provide personal information, access codes or financial data and then use them for their own use and consumption. This set includes scams based on links to flirtatious sites, e-mails that push you to connect to your bank's website to change your credentials following a hypothetical unauthorized access (fake-login, password-grabbing), offers of work or easy earning (skimming, identity theft) and so on.
It is clear that these expedients, while not based on sending attachments, are often based on the use of equally elaborate spoofing techniques. For this reason, learning to recognize the latter is absolutely essential.
Website-hosted malware
We mentioned earlier that over half of malware infections occur via e-mails. Wanting to shift the analysis to the other (almost) half, we can say with certainty that a large part of the slice is reserved for malware spread through software downloaded - more or less consciously - from websites and web services. This diffusion technique is in turn divided into two main sections: the voluntary download and the involuntary download.
Voluntary Download
Voluntary download infections are those that affect the user when he downloads software that corresponds more or less exactly to what he wanted to download: a program to listen to music, to find pirated software or to watch a funny video . In all cases, the user does not download through a secure channel, but is convinced - by a bad search, an ad banner or an unverified link - to download something that turns out to be - or contains - a malware. In some cases the malware comes into play immediately, allowing the user to immediately realize the mistake made; in other cases, more subtle and (unfortunately) very frequent, the downloaded program seems to work correctly and the malware appears only after a few days / week: a period of time more than enough to convince the victim that "he didn't do anything wrong", a statement that invariably clashes with the obvious skepticism of those called to solve the problem.
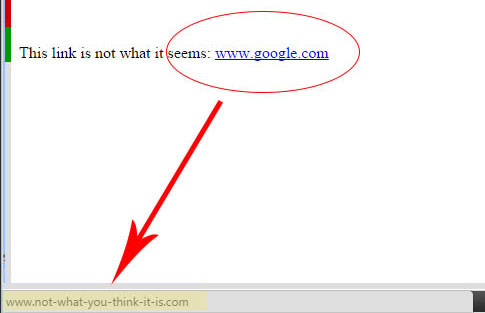
The techniques to defend against this type of attack are quite similar to those already mentioned in the paragraph on E-Mail: it is necessary to develop a particular level of attention to detail, this time focusing on the specific aspects that allow us to define and verify the identity. of the website. Among these, the most important is certainly the Uniform Resource Locator, otherwise known as the URL. For the uninitiated, we are talking about the web address of the site we intend to connect to. The considerations to be made on the URL are very similar to those already described in the paragraph relating to the Sender of the E-Mail message:. You must pay attention to how it is written, bearing in mind that what you see on the page does not always correspond to what you are actually going to visit. The following image makes the concept clear:
When your mouse passes over the link on which you intend to click, it is advisable to spend a fraction of a second to check if the destination - which you will find indicated at the bottom left. Never assume that the site you are on has an interest in giving you correct information on the URLs it presents: on the contrary, in most cases its interest is to make you click as much as possible, possibly on the links that produce a annuity - that is, sites that, at best, want to sell you something.
Having established that it is a good idea not to click on a URL presented in a dishonest way, let's see how to recognize potentially dangerous links with the naked eye. The first thing to check is the so-called scheme, that is the part that precedes the colon and the two slashes: in most cases you will find http or https. The first distinguishes sites that transmit their pages in an unencrypted way, while the second is reserved for those portals that have a security certificate issued by a third-party body. Since the certificate is issued only following a verification process, carried out by the entity, of the identity of the applicant, it is correct to state that https sites provide additional guarantees as, beyond the higher level of security of the transmitted data, they are managed by a verified company. This does not necessarily make them immune to threats or dangers, but it certainly constitutes an additional level of assurance over sites that use the traditional scheme.
The second component to check in a URL is the communication port used: in most cases this is not present, which means that the server hosting the site uses the default port (80 for http, 443 for https), which as such it does not need to be mentioned in the URL. In some cases, however, the port is explicitly specified, a sign that the server has been configured to serve the site via a non-standard port. While this isn't necessarily bad, a site open to the public - and therefore interested in making as many accesses as possible - is unlikely to use a non-standard port. Think of a shop that hides its entrance instead of advertising it: either it is an exercise open only to a very select clientele, or there could be something wrong. Keep in mind that the sites that intentionally host Malware have every interest in going unnoticed, limiting themselves to attracting victims by means of e-mails, flirtatious sites and phishing / scamming techniques similar to those already described.
The third thing to check is the address, not only in a syntactic sense - cf. paragraph relating to the Sender - but also and above all in relation to the expected topic: it is obvious that an e-mail that speaks of an invoice or receipt to be read and which offers a link to www.winningbets.it for this purpose will not be considered reliable. At the cost of repeating myself: get used to always checking the link at the bottom left before making the fateful click: once you'll start trying, it will eventually become automatic.
Involuntary Download
The infections from Involuntary Download are even more subtle than the previous ones: these infections strike the user treacherously, finding a way to settle on the hard disk by passing below his threshold of attention. Such category includes the so-called sponsored software, i.e. those products whose installation is offered during the installation procedure of another software - which happens thanks to a paid agreement entered into with the latter, which is therefore an accomplice - or that are downloaded and installed by other malware already present and active on the system.
To defend against this unhealthy practice, it is necessary to get rid of another bad habit, a close relative of the selective and superficial reading I mentioned earlier: the tendency of many users to pay little or no attention to disclaimers, warnings and information messages produced during the installing software, downloading applications, using particular features or browsing the web. It is once again worth remembering that the goal of the software you are using - be it a free access website, a freeware application or other free tool - is almost always to take over your clicks, your time and why not. hopefully your money: this is why, in most cases, accepting all conditions, ticking all checkboxes and / or accepting "valuable" advice during an installation is not a good idea. Be smart and never let your guard down, always read everything you are told and always think very carefully before clicking on buttons like OK, Accept or Confirm. Always try, if possible, to install your applications by selecting the manual mode and paying attention to the various stages of the process: not only will you avoid Malware, but you will also prevent your Hard Disk from filling up with useless programs or that are of no use to you. . Maintaining control over your system also means avoiding wasting memory and disk space by authorizing the installation of unknown software.
There is not much to say, except that it is a good idea to refrain from clicking on banner ads. Mind you, most of the ads on the web are controlled and verified by the companies that manage the Ads Publishing Network (Google AdSense above all): the possibility of hitting a Malware download by clicking on an ad is very low. The problem is in what is called a "double jump" - that is, an ad unit that points to a dangerous site within a web page reached via a massive - but often completely regular - advertising campaign. The purpose of this strategy is all too obvious: to exploit a part of the induced originating from an Ads Publishing Network using as through an intermediate and "clean" website in order to pass the checks unscathed and avoid the ban. The intermediate site can be controlled by those who distribute the Malware or, more frequently, unaware and unaware (if not for the agreements made with the dealer): in both cases it is a good idea to stay away from such sites, not infrequently dedicated to a use of the Internet that is to say the least objectionable: binary options, creative finance, pirated software, games and ringtones for mobile phones, erotic / sexual gossip news, itchy photogalleries and so on.
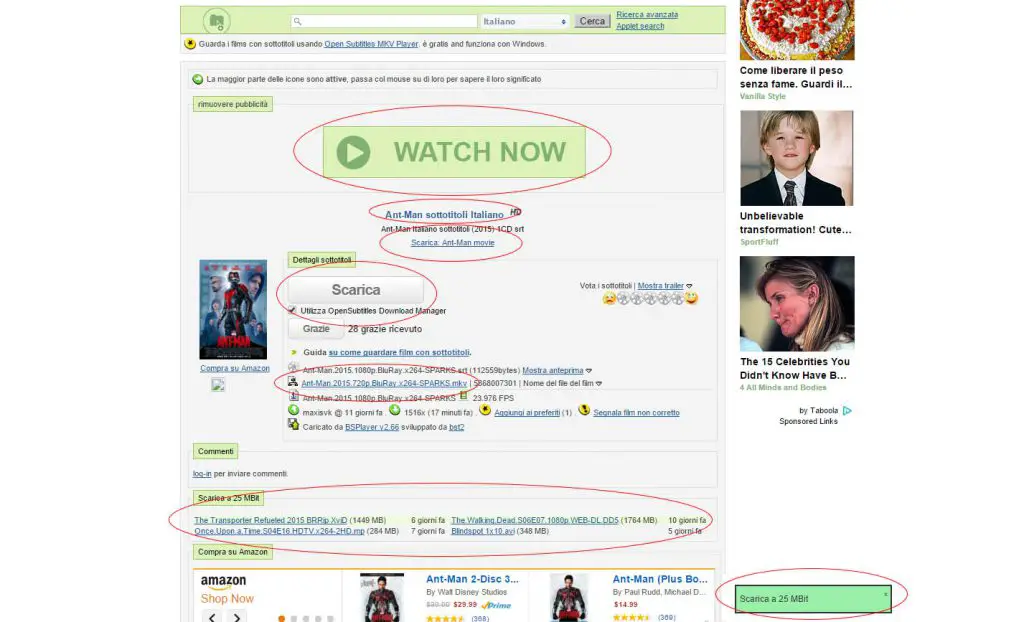
It is also fundamental to learn to recognize the ad units from the legitimate links present within the site. Don't underestimate this, there are cases where some experience is needed. Take for example the following image, related to a page that offers the free download of the subtitles of the Ant-Man movie:
How many of these links are actually banners or links to ad units? The answer is, all but one. And even that, if the checkbox below is not removed (enabled by default), leads the unwary author of the click to the apparently mandatory download of a potentially unwanted application and not at all indispensable for the download of the subtitles in question.
Treatment
After describing the main prevention techniques aimed at preventing Malware from entering our system, it is time to see what we can do if our efforts prove insufficient. For an exhaustive discussion of infection containment and elimination techniques, roughly suited to all the main threats, refer to the following posts:
- Malware infection – what to do and how to deal with it
- 7 Precautions You Should Follow to Protect Your System Against Malware
- How to prevent a Data Breach: Malwares, Viruses, Hackers, Phishing, Identity Theft & more