Table of Contents
In this article we will provide a general overview of the main concepts behind the World Wide Web as we know it today: the HTTP protocol, used by the browser to communicate with web servers; SSL / TLS certificates, essential for establishing secure and verified connections; Domain Name Servers (DNS), responsible for resolving domain names; Uniform Resource Locators (URLs), sequences of characters that uniquely identify the location of web pages; Distributed Denial of Service (DDoS) attacks, used to compromise the normal functioning of web services.
The HTTP(S) protocol
An acronym for Hypertext Transfer Protocol: it's the application layer protocol used by the browser to transmit web pages (HTML) and a series of other related formats (scripts, images, etc.). When the final S (Secure) is present, the communication takes place via an encrypted connection obtained through asymmetric encryption via Transport Layer Security (TLS) and a certificate installed on the server, otherwise, the communication takes place in clear text.
HTTP request/response cycle
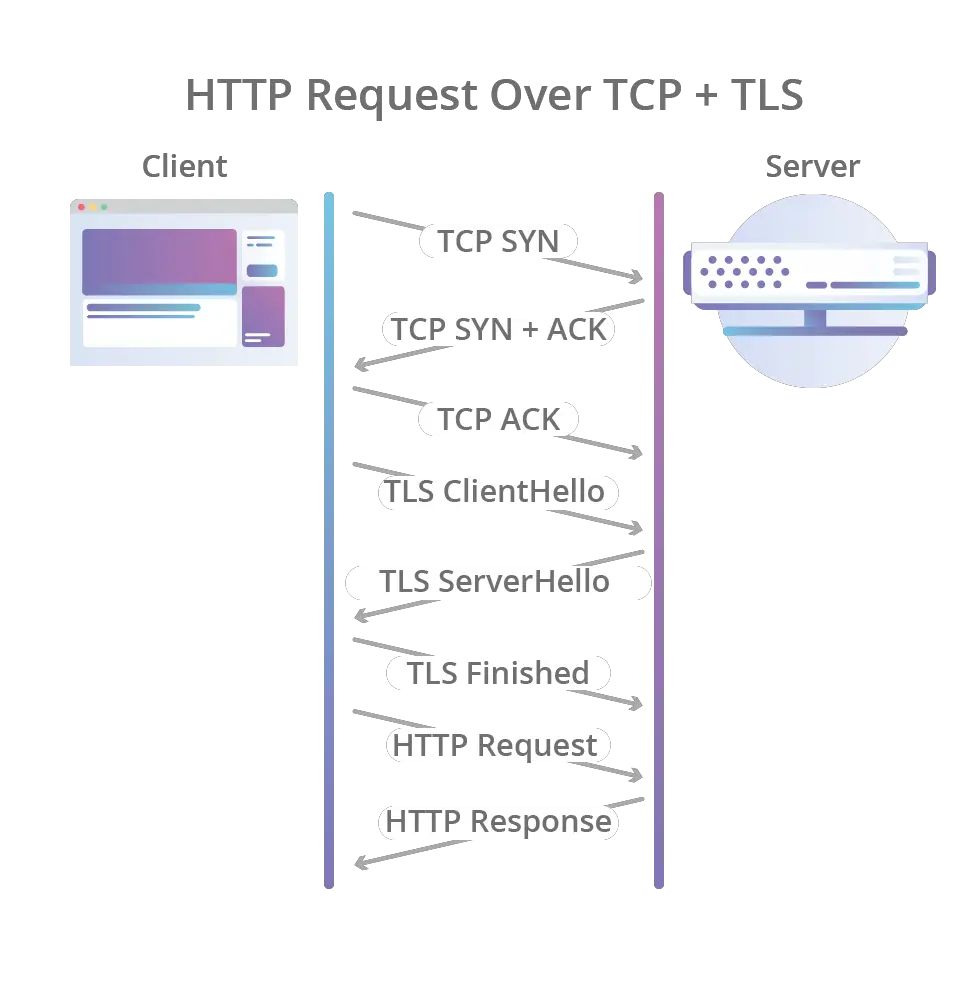
The browser interacts with websites via HTTP (S) using a client/server type architecture, where the client is the browser and the server is the webserver (IIS, Apache, NGINX, etc). The two fundamental points of this interaction are the following:
- the client connects to the URL managed by the server using a TCP port (typically 80 for HTTP and 443 for HTTPS) and executes a request (HTTP Request)
- The server returns a response (HTTP Response)
In the case of connection via HTTPS, both the request and the response are encrypted using a TLS channel negotiated through the SSL / TLS certificate installed on the server immediately after the connection and before sending the data. Below is the complete diagram of the HTTPS interactions between client and server.
SSL/TLS Certificates (HTTPS)
A digital certificate is an electronic document issued by a Certification Authority (CA) which certifies the unique association between a public key and the identity of a subject (usually an organization). This certificate, together with the private key uniquely associated with it, allows the webserver to negotiate an encrypted connection with the connecting clients (browsers). This connection takes place with a cryptographic protocol such as SSL (Secure Socket Layer), used until a few years ago, or the subsequent TLS (Transport Layer Security), which is in fact an improved version of its predecessor and is today the only one to be used as SSL is no longer considered secure enough.
The TLS certificate serves two main purposes:
- Guarantee the identity of the website visited, reducing the risk of falling victim to scams based on DNS spoofing, domain spoofing, and other similar techniques.
- Guarantee, thanks to asymmetric encryption, the authenticity, integrity, and confidentiality of the data transmitted by the client (request) and received by the server (response).
Given the importance of these two aspects, today practically all websites are published via HTTPS, with the HTTP port (80) used only as a redirect over HTTPS.
Domain Name System (DNS)
The Domain Name System (an acronym for DNS, in Italian domain name system) is the system for assigning names to the nodes, or IP addresses, that make up the internet. The best way to imagine it is to think of a sort of distributed database, in which domain names (hostnames) and their association with their IP addresses are stored.
A domain name (hostname) consists of a series of strings separated by periods, for example, www.wikipedia.org. In detail:
- The rightmost segment (org) is called Top Level Domain and is usually related to the country of origin.
- What precedes it (wikipedia) is called second-level domain and is typically formed by a word chosen at will; this is what is purchased from the domain provider (for example Aruba or GoDaddy) and is typically called a "web domain".
- What precedes it (www), if present, is called third-level domain; second-level domains can be created at will by the owner of the second-level domain.
Uniform Resource Locator (URL)
A Uniform Resource Locator, better known as a URL, is a sequence of characters that uniquely identifies the address of a resource on a computer network (such as the internet).
It consists of six parts, some of which are optional:
protocol://[username[:password]@]host[:porta][</percorso>][?querystring][#fragment]
In some cases, the acronym URI (Uniform Resource Identifier) is used instead of URL, a more generic term that includes both URLs and other existing unique identifiers, such as the ISBN codes of books.
DDoS Attack
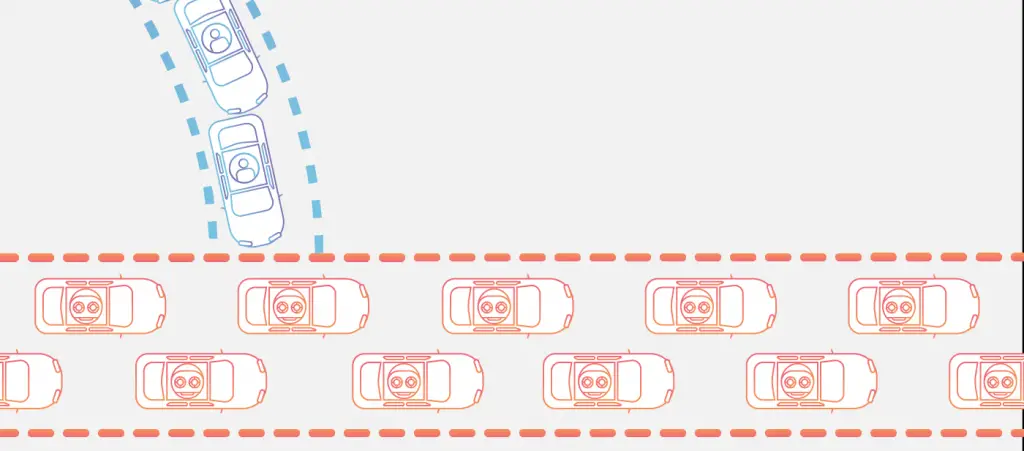
A DDoS attack (an acronym for Distributed Denial of Service) is a type of attack that is conducted against a server (typically a web server) with the aim of compromising its operation. The most common attack method involves creating a huge amount of HTTP (S) connections directed simultaneously to the target server, in order to saturate its management capabilities, thus preventing "legitimate" clients from using the service. It is, in essence, an attack that aims to create a sort of "traffic jam".
This type of attack is relatively simple to carry out and is very effective: for this reason, it is one of the most used. However, this is not a particularly dangerous attack from the point of view of security or data protection as, even if successful, it does not allow the attacker to access the servers or steal information of any kind (except in extreme cases related to side effects that could take place on the server following the overload of requests): it should therefore be considered as a nuisance action against the service object of the attack and its regular users.