A rather common requirement in Windows-based networks is restricting the access to the shared file system for some specific machines. The reasons for wanting that can be many: security issues, simplifying the user experience for non-expert operators and so on. For almost all of them you shouldn't use that machine IP Address: Windows Security Model is designed to work per-user, not per-IP, and there are good reasons for that: IPs can be spoofed, just to say one, expecially in a LAN. For this reason, your best choice to restrict any potentially unauthorized access to your network shared resources would be using the built-in ACL, using the good old Properties > Security tab.
However, there are some edge-case scenarios where security is not an issue - or we already dealt with it in a secure way - and we just want to block one or more IP addresses from accessing our shared printers, folders & files. The best way to do that would be using the built-in Windows Firewall (or any other firewall) to block the TCP ports used by SMB-in and/or SMB-out connections. For those who don't know, SMB is the acronym for Server Message Block, a sharing protocol for files and printers used by Windows operating systems since the early '90s.
The port block can be performer either at client level, assuming that the user cannot disable that firewall rule, or using the firewall installed on the machine(s) hosting the files, folders & printers which we want to not share. The proper choice would depend upon the given scenario: if we have to block a single machine from accessing multiple shares located on different IP Addresses, the first option would probably be the only viable one; conversely, if we want to block multiple clients from accessing a share hosted on a specific server, the latter will be the most effective one.
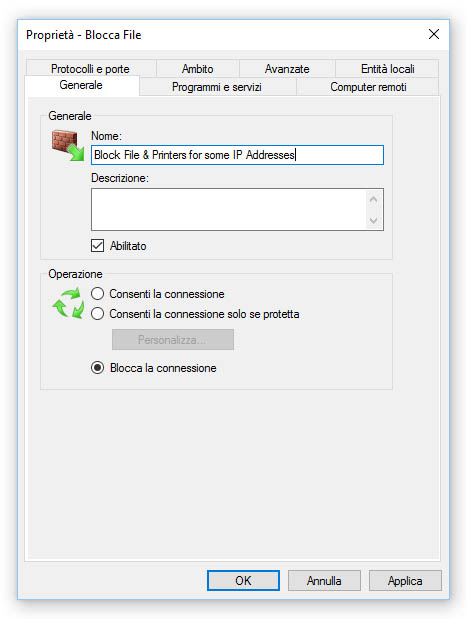
Whenever we want to perform the block on the connecting client side, we need to open that client's Windows Firewall and create a new outbound rule to block the TCP port 445 for the IP address of the machine hosting the share; conversely, if we want to shield the host from unwanted access we need to open the host Windows Firewall and create a new inbound rule blocking the TCP port 445 for the IP address of the client(s) we want to prevent access from.
IMPORTANT: In case we want to also disable the SMB connections via NetBIOS API (highly recommended if you want to prevent the access from older Windows XP / Windows 2000 clients) we should also block ports TCP 137, 139 (NetBIOS-Session) and UDP 137, 138 (NetBIOS-Name).
Either way, the Scope tab should look like the following screenshot:
If the machine you want to block has more than one IP Address, you might want to put all of them in the Remote Address list; also, remember to specify the IPv4 and IPv6 addresses for the machine you want to block.
That's it for now: happy blocking!